OpenID Connect
Important!
Never provide your access_token, refresh_token or client_secret to a web browser or other end-user agent. Instead, maintain a separate session and persist this data in a location accessible only by your application (e.g. do not store the access_token in a cookie).
Contact api-support@sparkplatform.com for further guidance.
OpenID Connect (OIDC) is a simple identity layer on top of the OAuth 2.0 protocol. The standard is controlled by the OpenID Foundation.
Authorization Code Walkthrough
The Spark® Identity Provider (IdP) adds an extension to support OAuth 2.0 requests inside a single OpenID request.
All OpenID Connect requests must be made using HTTPS.
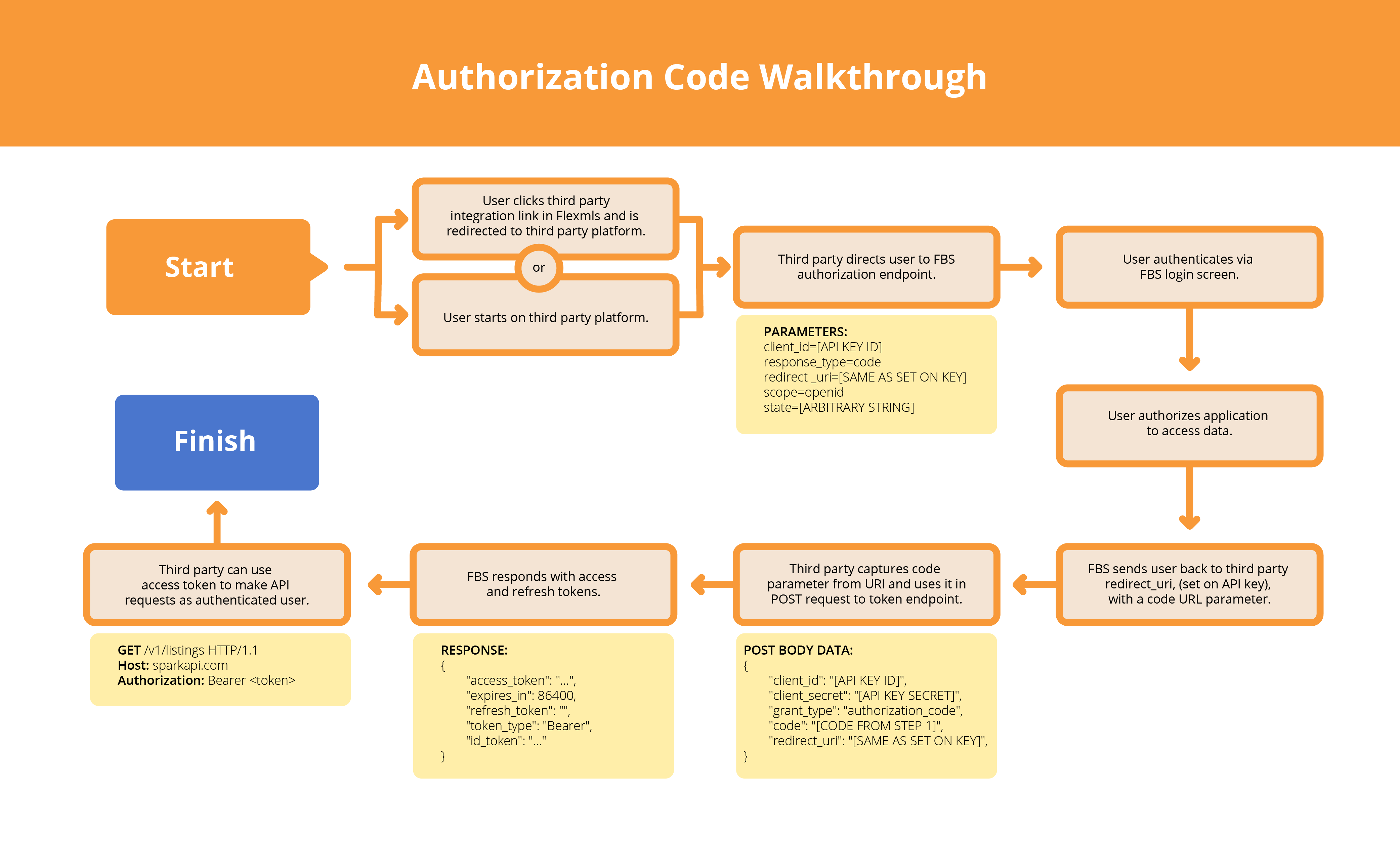
The typical OpenID Connect/OAuth2 flow with Spark API can be broken down into four steps:
Step 1 - Obtaining User Authorization
Endpoints:
You can obtain our OpenId Configuration information at https://sparkplatform.com/.well-known/openid-configuration. As specified in the OpenID Connect Discovery Specification. Most programming languages will have libraries pre-built to easily integrate OpenID Connect.
See also section 3.1 of OpenID Connect Core.
First, the Flexmls user must authenticate with FBS and grant the third party access to their data. Once they do, they are returned to the third party platform with a code the third party will need to obtain an API access token. Please be aware that the client_id parameter corresponds to the API key’s “OAuth Key” unique identifier included in the API key credentials email.
1. The third party begins by redirecting the Flexmls user they wish to authenticate to FBS’s authentication endpoint with the necessary parameters.
https://sparkplatform.com/openid/authorize?client_id=Your_OAuth_Key&scope=openid&response_type=code&redirect_uri=https://example.com/callback&state=abcdefgh&nonce=zyxwvuts
2. The user is asked to authenticate via a Flexmls login page (if they are not already logged in).
3. If this is the first time this user is authenticating via this API key, they’re asked to accept that they’re granting the third party access to Flexmls data. Note that this step can be skipped in some cases, particularly for Flexmls integrations with third party platforms.
4. Once the user has been authenticated by FBS and granted their approval for third party data access, FBS redirects the user back to the third party. The redirect URI set on the OIDC API key determines where the user is redirected to, and should always be a URI controlled by the third party.
5. A code=[value] parameter is appended to the redirect URI when the user is returned to the third party. The third party must capture the code parameter and use its value to complete the token exchange step. Be advised that the code must be inputted in the POST request to obtain the access token.
https://example.com/callback?state=abcdefgh&code=c07pue969wqlz6u5clvm2gypz
Note that OpenID responds with many more parameters, but these two are the most important for an OAuth 2 example. You will use the code within the callback to request a token shown in the Token Exchange example below.
Step 2 - Token Exchange
See also OpenID Connect Core Token Endpoint.
After the user has successfully authenticated with FBS and authorized the third party application’s data access, and the third party has captured the code parameter appended to the redirect URI when the user is returned to them from FBS, the third party exchanges that code for an access token that allows them to hit the Spark API as the user that was just authenticated.
They do so by sending a POST request, with the body data specified below, to the https://sparkplatform.com/openid/token resource:
{
"client_id": "[client_id]",
"client_secret": "[client_secret]",
"grant_type": "authorization_code",
"code": "[code]",
"redirect_uri": "[redirect_uri]",
}
| Attribute | Description |
|---|---|
client_id |
This is your OAuth client ID, also known as the OAuth Key provided via email by FBS. |
client_secret |
This is your OAuth client secret provided by FBS via email. |
grant_type |
This is always set to authorization_code. |
code |
This is the value of the code obtained in step 1. |
redirect_uri |
The value of the URI to which the user will be redirected upon completion. The domain must match that which is registered with FBS. (We encourage you to use HTTPS for your redirect URI.) |
{
"access_token": [access_token],
"expires_in": 86400,
"refresh_token": [refresh_token],
"token_type": "Bearer",
"id_token": [id_hash]
}
{
"error": "[error_code]",
"error_description": "Detailed message here"
}Step 3 - Requesting Data
Authorization: Bearer [access_token]The access token returned by the response to the third party’s POST request can now be used for requests to the Spark API or RESO Web API. The authenticated user is considered the current API user for all requests made with this access token. See this documentation for how to make authenticated API requests with this access token. The third party can identify the user by making a request to the Spark API’s my/account service with the access token from the token exchange step.
https://replication.sparkapi.com/v1/my/accountThis is the basic workflow for using OIDC to implement SSO integrations with Flexmls and identify Flexmls users. Read on for more advanced functions.
Step 4 - Refreshing Expired Sessions
Access tokens expire after 24 hours, yet it would be undesirable to have to redirect end users to the OAuth 2 authorization flow once a day. The refresh flow is a remedy to this.
HTTP/1.1 401 Unauthorized
WWW-Authenticate: Bearer realm='Flexmls API', error='invalid_token'
{
"D": {
"Success": false,
"Message": "Session token has expired",
"Code": 1020
}
}
To refresh the access token, POST the following JSON data to the API's OAuth Access Token service at https://sparkplatform.com/openid/token using HTTPS:
{
"client_id": "[client_id]",
"client_secret": "[client_secret]",
"grant_type": "refresh_token",
"refresh_token": "[refresh_token]"
}| Parameter | Description |
|---|---|
client_id |
This is your OAuth client ID provided by FBS. |
client_secret |
This is your OAuth client secret provided by FBS. |
grant_type |
Set this to refresh_token . |
refresh_token |
This is the value of the refresh token obtained from the initial access token grant. |
{
"access_token": "example_new_access_token",
"refresh_token": "example_new_refresh_token",
"expires_in": 86400,
"token_type": "Bearer",
"id_token": [id_hash]
}{
"error": "[error_code]",
"error_description": "Detailed message here"
}Deleting Access Tokens
/<API Version>/oauth2/token/<Token>
| HTTP Method | Description | Notes |
|---|---|---|
| DELETE | Destroy an existing token, expiring it immediately. |
Delete Request
Parameters:
- None
DELETE Response
The standard success/fail response is returned.
Single Logout
Spark Platform provides a single log out service that can be accessed directly from the following URI:
https://sparkplatform.com/openid/logoutThe Single Logout process destroys the existing cookie at our OpenID Connect endpoint, requiring the user log in the next time they are directed to the endpoint. It also destroys custom sessions for other applications built on the Spark Platform, so long as those applications have specified a Single Logout URI in the Spark Store.
| Parameter | Description |
|---|---|
client_id |
This is your OAuth client ID provided by FBS.
Only required if post_logout_redirect_uri is
provided. |
post_logout_redirect_uri |
If provided, the user will be redirected back to this URI after
logging out. This must match the redirect_uri for the
client_id. |
state |
(Optional) Will be returned to your post_logout_redirect_uri.
See this documentation
for preferred usage. |
Revocation
Spark Platform provides a revocation service that can be accessed directly from the following URI:
https://sparkplatform.com/openid/revokeYou can direct users to the revocation endpoint if you want to allow them to remove your application's authorization. Which will require the user's consent for API access the next time you make a request on their behalf. You can also send a POST request to the revoke endpoint to invalidate your keys. Look at Section 2.1 of OAuth 2.0 Token Revocation for more information.